Cyber Security Awareness
Technology
YOU are the most powerful defense against cyber attacks.
Cyber Security Tip #1 – Phishing
Phishing is a cybercrime using a tactic in which a hacker targets you by email and poses as someone you may know. Their goal is to get sensitive data such as your password, banking and credit card details, and any other personally identifiable information.
Spear Phishing is a refined version of phishing. The hacker changes their email display name to emulate someone you know, thus gaining your trust. These are personalized attacks that target a specific victim. If you reply to the hacker, they are fairly certain you fell for the trick and then begin giving you instructions to get more information from you.
We have seen an increase in these attempted attacks in recent months right here at SJC.
Things to look out for that should send up red flags:
- Too good to be true – Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately.
- Sense of urgency – A favorite tactic amongst cybercriminals is to ask you to act fast because the super deals are only for a limited time.
- Hyperlinks – A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it.
- Attachments – If you see an attachment in an email you weren’t expecting or that doesn’t make sense, don’t open it! They often contain payloads like ransomware or other viruses.
- Unusual sender – Whether it looks like it’s from someone you don’t know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general, don’t click on it!
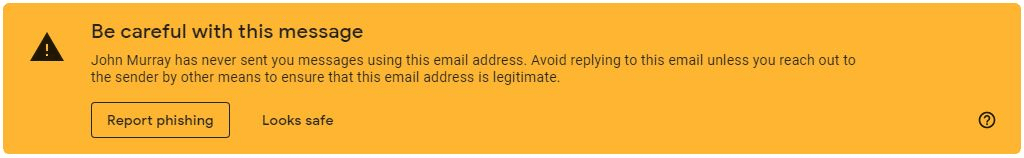
Using Google apps on your phone, tablet or other device will give you an extra layer of security. Gmail will detect that the sender is not someone you may have contacted before and will issue a warning like this:
Other email programs like Outlook or Apple email will not give you these warnings.
Lastly, if you get a suspicious email and are not sure about it, forward it to the IT team at iteam@sjcme.edu. An IT technician will investigate to determine if it is legitimate or not.
Cyber Security Tip #2 – Passwords
A good password is one that makes it more difficult for a hacker to crack. SJC requires a complex password; one with letters, numbers, and special characters. That’s a good start, but there is more you can go. Here are some tips for a strong password.
Long password – Mathematically speaking, the difference between a weak password and a strong password is the number of characters available, and hence the number of possible combinations available to construct a password based on those characters.
Passwords should not be easy to guess. – As human beings we tend to follow the same patterns when selecting passwords – things like pet’s names, a favorite sport, or even the word ‘password.’ Not to mention a sequential list of number like 123456. Common passwords are extremely easy to guess, and should be avoided.
There is no denying; passwords are a pain. With so many accounts, both work related and personal, it’s nearly impossible to manage them all.
Browsers have their own built-in password management. You can have the browser remember the password for you.
There are also 3rd party applications that will manage passwords for you. Some of them are free up to a certain number of passwords. These are just a few of many available:
- Dashlane (www.dashlane.com)
- Lastpass (www.lastpass.com)
- LogmeOnce (www.logmeonce.com)
Don’t ever think you’re “not important enough” to be attacked. It doesn’t matter how small or big our organization is or how much important information you as an individual think you might have, if you’ve got money or data (passwords, client data, emails, etc.) you are an attractive target.
Stay Secure. Have good passwords.
Cyber Security Tip #3 – Multi-Factor Authentication
Multi-Factor Authentication is sometimes called Two-Factor Authentication. It means that you use more than one piece of information to verify your identity when logging into a system. The first piece of information is usually your password. This would be considered the 1st factor.
During the login process, you will be prompted to interact in some way to verify the 2nd factor. The method used for the 2nd factor can vary. Here are some of the most widely used options:
- The login process sends you a code via text, or sometimes a phone call, and you enter the code into the web site you are trying access.
- Getting a push notification to an authentication app on your phone, and verified with a code or fingerprint.
- Swiping a card.
- Answering a security question.
- Attaching a USB hardware token to your computer.
Why is Multi-Factor Authentication so important? Because computer technology, specifically computer processing speeds, have increased exponentially. A computer with hacking software can produce more than 500 million passwords a second. Some sophisticated programs can crack a 14-character alphanumeric password in about 160 seconds. Hackers use something called a ‘brute force” attack. They use these hacking programs to fire thousands of passwords at a select target. With so many combinations attempted, odds are that some of them will get through.
Passwords just aren’t that secure anymore. Multi-Factor Authentication adds another level of security for your protection. You would be wise to use it when you can.
Cyber Security Tip #4 – Mobile Devices
With more and more of our daily computing done on mobile devices, here are some steps you should take to ensure your data is safe.
- Lock your device with a password, pin, or biometric fingerprint or facial recognition.
- Never leave your devices unattended. If you need to leave phone or tablet for any length of time – no matter how short – lock it up so no one can use it while you are gone.
- Do not “Root” your Android or “Jailbreak” your iPhone. It is basically like running a computer in administrator mode. While it’s possible to run a rooted phone safely, it’s definitely a security risk. Some exploits and malware need root access to function and are otherwise harmless even if you do somehow install them. If you don’t have a good reason to root your phone or tablet, just don’t open yourself up to that possibility.
- Do not open or follow links from texts or email from misleading URL, suspicious or untrusted sources.
- Don’t download apps from third-party sites. Only use official apps from Google Play or iTunes.
- Be cautious when connecting to publicly available Wi-Fi hotspots, and avoid accessing sensitive data unless with adequate security protection.
- Sensitive browsing, such as banking or shopping, should only be done on a device that belongs to you, on a network you trust. Whether it’s a friend’s phone, a public computer, or a cafe’s free Wifi – your data could be copied or stolen.
- Back up your device and it’s data regularly.
- Watch what you are sharing on social networks. Criminals can befriend you and easily gain access to a shocking amount of information – where you go to school, where you work, when you’re on vacation – that could help them gain access to more valuable data.
- Completely clear all data and settings on your mobile device before disposal.
Cyber Security Tip #5 – Social media quizzes
They seem innocent enough… Quizzes on social media that have you answer questions like; “15 questions about my childhood” or “What Disney character are you?”. Your series of answers may give hackers insight to who you are, and allow them to decipher enough information to breach your private data.
Where do quizzes come from? Some social media quizzes do have legitimate uses and are used frequently by different companies to market their products. Other quiz sites are fan based and created by individuals. Quizzes can be created by anyone in just a few minutes.
Sometimes you see a single answer quiz such as “What is your favorite dogs name?” While your answer may not seem like much information for someone to use, it very well could be the gateway to your bank account. Think about some of the canned security questions that appear when you create a new account: “mother’s maiden name; street you grew up on; favorite dogs name”. The person who receives the responses of the quiz now has a bit of information that could be used against you.
Be wary of quizzes.
- Make sure they are from legitimate sources.
- Never respond to a login request when taking a quiz.
- Never grant the quiz access to your social media account.
- Never download anything from a quiz if you are prompted to do so.
- Know that all quizzes will get some sort of information from you.